Why Cybersecurity Should Be a Top Priority for New Businesses
Cybersecurity for startups is no longer a luxury, but a necessity. The digital landscape is fraught with threats, from data breaches to financial losses, and reputational damage. A single security incident can have devastating consequences for a startup, including loss of customer trust, intellectual property theft, and even bankruptcy. In fact, according to a recent study, 60% of small businesses that experience a cyberattack go out of business within six months.
Despite these risks, many startups neglect cybersecurity, often due to limited resources or a lack of expertise. However, this approach can be short-sighted. A strong cybersecurity posture can help protect a startup’s most valuable assets, including customer data, intellectual property, and competitive advantage. By prioritizing cybersecurity, startups can mitigate risks, ensure business continuity, and build trust with customers and investors.
Moreover, cybersecurity for startups is not just about protecting against external threats. Insider threats, such as employee negligence or malicious activity, can be just as damaging. A comprehensive cybersecurity strategy should include measures to prevent, detect, and respond to insider threats, as well as external threats.
Fortunately, there are steps startups can take to improve their cybersecurity posture. This includes implementing basic security measures, such as firewalls, antivirus software, and encryption, as well as more advanced measures, such as threat intelligence and incident response planning. By taking a proactive approach to cybersecurity, startups can reduce their risk exposure and protect their digital future.
Ultimately, cybersecurity for startups is not just a technical issue, but a business imperative. By prioritizing cybersecurity, startups can build trust with customers, protect their intellectual property, and ensure business continuity. In today’s digital landscape, there is no excuse for neglecting cybersecurity. Startups that fail to prioritize cybersecurity do so at their own peril.
Assessing Your Startup’s Cybersecurity Risks
Cybersecurity for startups is a complex and ever-evolving challenge. To protect their digital assets, startups must first understand the risks they face. A thorough risk assessment is essential to identifying vulnerabilities in a startup’s systems and processes. This includes evaluating the likelihood and potential impact of various threats, such as phishing, ransomware, and insider threats.
Phishing, for example, is a common threat that can have devastating consequences. According to a recent study, 76% of businesses reported being a victim of phishing in the past year. To mitigate this risk, startups can implement robust email security measures, such as spam filtering and email encryption. They can also educate employees on how to identify and report suspicious emails.
Ransomware is another significant threat that can cripple a startup’s operations. This type of malware encrypts a victim’s files and demands a ransom in exchange for the decryption key. To protect against ransomware, startups can implement regular backups, use antivirus software, and ensure that all software and systems are up-to-date.
Insider threats are also a significant concern for startups. These threats can come from employees, contractors, or partners who have authorized access to a startup’s systems and data. To mitigate this risk, startups can implement strict access controls, monitor user activity, and provide regular security training to employees.
To conduct a comprehensive risk assessment, startups can follow these steps:
1. Identify assets: Determine what digital assets need to be protected, such as customer data, intellectual property, and financial information.
2. Assess vulnerabilities: Evaluate the likelihood and potential impact of various threats, such as phishing, ransomware, and insider threats.
3. Implement controls: Put in place measures to mitigate identified risks, such as email security, antivirus software, and access controls.
4. Monitor and review: Regularly monitor and review the risk assessment to ensure that it remains accurate and effective.
By following these steps, startups can develop a comprehensive risk assessment that helps them understand and mitigate the cybersecurity risks they face.
Building a Strong Cybersecurity Foundation
A strong cybersecurity foundation is essential for protecting a startup’s digital assets. This foundation consists of several key components, including firewalls, antivirus software, and encryption. By implementing these measures, startups can significantly reduce the risk of cyberattacks and protect their intellectual property, customer data, and competitive advantage.
Firewalls are a critical component of a startup’s cybersecurity foundation. They act as a barrier between the startup’s network and the internet, blocking unauthorized access and malicious traffic. To ensure the effectiveness of a firewall, startups should configure it to block all incoming and outgoing traffic by default, and only allow specific traffic that is necessary for business operations.
Antivirus software is another essential component of a startup’s cybersecurity foundation. It helps to detect and remove malware, including viruses, Trojans, and spyware. To ensure the effectiveness of antivirus software, startups should keep it up-to-date and run regular scans of their systems and data.
Encryption is also a critical component of a startup’s cybersecurity foundation. It helps to protect data both in transit and at rest, making it unreadable to unauthorized parties. To ensure the effectiveness of encryption, startups should use strong encryption algorithms, such as AES, and implement encryption protocols, such as SSL/TLS.
In addition to these components, startups should also implement other security measures, such as intrusion detection and prevention systems, and security information and event management systems. These measures can help to detect and prevent cyberattacks, and provide real-time monitoring and incident response capabilities.
To ensure the effectiveness of a startup’s cybersecurity foundation, it is essential to regularly review and update security measures. This includes updating software and systems, patching vulnerabilities, and conducting regular security audits and risk assessments.
By building a strong cybersecurity foundation, startups can protect their digital assets and reduce the risk of cyberattacks. This foundation is essential for protecting a startup’s intellectual property, customer data, and competitive advantage, and for ensuring the long-term success and growth of the business.
In the context of cybersecurity for startups, a strong foundation is critical for protecting against emerging threats and trends. By implementing the components of a strong cybersecurity foundation, startups can stay ahead of the threats and protect their digital assets.
How to Develop a Cybersecurity Strategy for Your Startup
Developing a comprehensive cybersecurity strategy is essential for protecting a startup’s digital assets. A well-planned strategy can help prevent cyberattacks, reduce the risk of data breaches, and ensure business continuity. In this article, we will provide a step-by-step guide on how to develop a cybersecurity strategy for your startup.
Step 1: Define Security Goals
The first step in developing a cybersecurity strategy is to define your security goals. This includes identifying the types of data that need to be protected, such as customer information, financial data, and intellectual property. It also involves determining the level of security required to protect these assets.
Step 2: Identify Security Controls
Once you have defined your security goals, the next step is to identify the security controls that need to be implemented. This includes firewalls, antivirus software, encryption, and access controls. It also involves determining the types of security measures that need to be implemented, such as intrusion detection and prevention systems, and security information and event management systems.
Step 3: Establish Incident Response Procedures
Establishing incident response procedures is critical for responding to cyberattacks and minimizing the impact of a security breach. This includes developing a incident response plan, identifying the types of incidents that need to be responded to, and determining the procedures for responding to these incidents.
Step 4: Implement Security Measures
Once you have identified the security controls and established incident response procedures, the next step is to implement these measures. This includes configuring firewalls, installing antivirus software, and implementing encryption. It also involves training employees on security best practices and ensuring that they understand their roles and responsibilities in maintaining the security of the startup’s digital assets.
Step 5: Monitor and Review
The final step in developing a cybersecurity strategy is to monitor and review the security measures that have been implemented. This includes regularly reviewing security logs, monitoring for suspicious activity, and updating security measures as needed.
By following these steps, startups can develop a comprehensive cybersecurity strategy that protects their digital assets and ensures business continuity. Remember, cybersecurity for startups is an ongoing process that requires regular monitoring and review to ensure the security of digital assets.
Protecting Your Startup’s Data in the Cloud
As a startup, it’s likely that you’re using cloud services to store and manage your data. While cloud computing offers many benefits, such as scalability and cost savings, it also introduces new cybersecurity risks. In this article, we’ll discuss the importance of cloud security for startups and provide tips on how to protect your data in the cloud.
Cloud Security Risks for Startups
Cloud security risks for startups include data breaches, unauthorized access, and data loss. These risks can be mitigated by choosing a secure cloud service provider and implementing cloud security best practices.
Choosing a Secure Cloud Service Provider
When choosing a cloud service provider, it’s essential to consider their security posture. Look for providers that have a strong track record of security and compliance, such as SOC 2 or ISO 27001 certification. Additionally, ensure that the provider offers robust security features, such as encryption, access controls, and monitoring.
Implementing Cloud Security Best Practices
To protect your data in the cloud, it’s essential to implement cloud security best practices. This includes:
1. Encrypting data both in transit and at rest
2. Implementing access controls, such as multi-factor authentication and role-based access control
3. Monitoring cloud resources for suspicious activity
4. Regularly updating and patching cloud software and systems
5. Implementing a cloud security gateway to monitor and control cloud traffic
By following these best practices, startups can protect their data in the cloud and reduce the risk of cybersecurity breaches.
Cybersecurity for startups is an ongoing process that requires regular monitoring and review to ensure the security of digital assets. By prioritizing cloud security and implementing best practices, startups can protect their data and ensure business continuity.
Cybersecurity Best Practices for Remote Workers
As a startup, it’s likely that you have remote workers who access your company’s data and systems from outside the office. While remote work offers many benefits, such as increased flexibility and productivity, it also introduces new cybersecurity risks. In this article, we’ll discuss the cybersecurity risks associated with remote work and provide tips on how to mitigate them.
Cybersecurity Risks of Remote Work
Remote work introduces several cybersecurity risks, including:
1. Unsecured communication channels: Remote workers may use unsecured communication channels, such as public Wi-Fi or personal email accounts, to access company data.
2. Data encryption: Remote workers may not use encryption to protect company data, making it vulnerable to interception and theft.
3. Two-factor authentication: Remote workers may not use two-factor authentication, making it easier for hackers to gain access to company systems.
Best Practices for Remote Workers
To mitigate the cybersecurity risks of remote work, startups can implement the following best practices:
1. Secure communication channels: Use virtual private networks (VPNs) or secure communication channels, such as encrypted email or messaging apps, to protect company data.
2. Data encryption: Use encryption to protect company data, both in transit and at rest.
3. Two-factor authentication: Use two-factor authentication to add an extra layer of security to company systems.
4. Regular security updates: Regularly update and patch remote workers’ devices and software to prevent vulnerabilities.
5. Security awareness training: Provide regular security awareness training to remote workers to educate them on cybersecurity best practices.
By implementing these best practices, startups can protect their data and systems from the cybersecurity risks associated with remote work.
Cybersecurity for startups is an ongoing process that requires regular monitoring and review to ensure the security of digital assets. By prioritizing cybersecurity and implementing best practices, startups can protect their data and ensure business continuity.
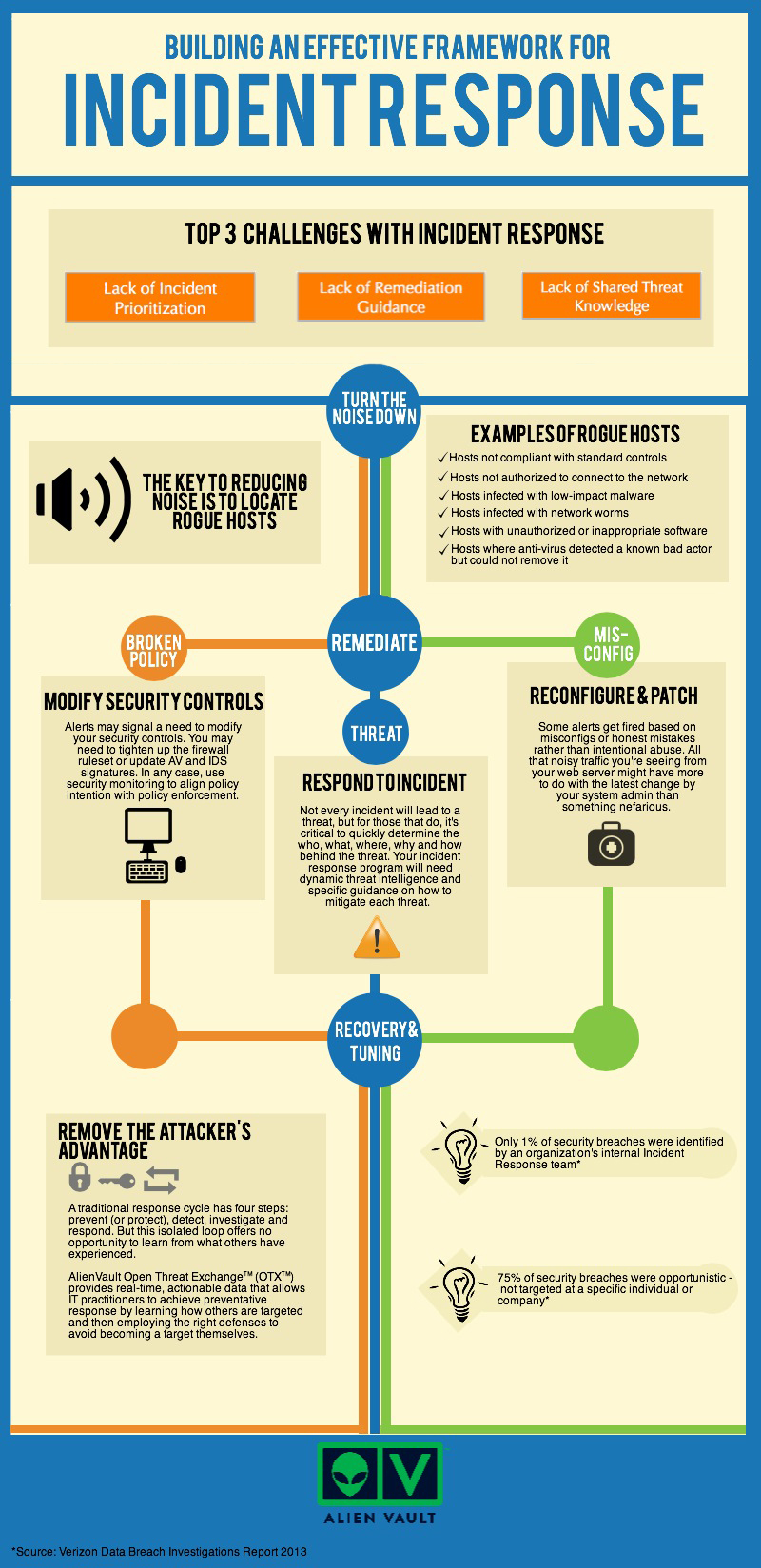
Incident Response Planning for Startups
Incident response planning is a critical component of a startup’s cybersecurity strategy. It involves developing a clear response plan, communication protocols, and post-incident activities to minimize the impact of a security breach. In this article, we’ll discuss the importance of incident response planning for startups and provide tips on how to develop an incident response plan.
Why Incident Response Planning is Important for Startups
Incident response planning is essential for startups because it helps to minimize the impact of a security breach. A security breach can result in significant financial losses, reputational damage, and loss of customer trust. By having an incident response plan in place, startups can quickly respond to a security breach and minimize the damage.
Components of an Incident Response Plan
An incident response plan should include the following components:
1. Clear response plan: Develop a clear response plan that outlines the steps to be taken in the event of a security breach.
2. Communication protocols: Establish communication protocols to ensure that all stakeholders are informed of the security breach and the response plan.
3. Post-incident activities: Develop post-incident activities to ensure that the security breach is fully contained and that steps are taken to prevent future breaches.
How to Develop an Incident Response Plan
To develop an incident response plan, startups should follow these steps:
1. Identify the incident response team: Identify the team members who will be responsible for responding to a security breach.
2. Develop a clear response plan: Develop a clear response plan that outlines the steps to be taken in the event of a security breach.
3. Establish communication protocols: Establish communication protocols to ensure that all stakeholders are informed of the security breach and the response plan.
4. Test and update the plan: Test and update the incident response plan regularly to ensure that it is effective and up-to-date.
By following these steps, startups can develop an incident response plan that helps to minimize the impact of a security breach and protect their digital assets.
Cybersecurity for startups is an ongoing process that requires regular monitoring and review to ensure the security of digital assets. By prioritizing incident response planning, startups can protect their data and ensure business continuity.
Staying Ahead of Emerging Cybersecurity Threats
As a startup, it’s essential to stay informed about emerging cybersecurity threats and trends. Cybersecurity threats are constantly evolving, and new threats are emerging every day. To protect your startup’s digital assets, you need to stay ahead of these threats and incorporate the latest threat intelligence into your cybersecurity strategy.
Why Staying Informed is Important
Staying informed about emerging cybersecurity threats is crucial for several reasons:
1. Protecting against new threats: New threats are emerging every day, and staying informed helps you protect against these threats.
2. Staying ahead of hackers: Hackers are constantly evolving their tactics, and staying informed helps you stay ahead of them.
3. Improving incident response: Staying informed helps you improve your incident response plan and respond more effectively to security breaches.
How to Stay Informed
To stay informed about emerging cybersecurity threats, you can:
1. Follow cybersecurity news and blogs: Follow reputable cybersecurity news sources and blogs to stay up-to-date with the latest threats and trends.
2. Attend cybersecurity conferences and events: Attend cybersecurity conferences and events to learn from experts and stay informed about the latest threats and trends.
3. Join online communities: Join online communities, such as cybersecurity forums and social media groups, to stay informed and connect with other cybersecurity professionals.
4. Subscribe to threat intelligence feeds: Subscribe to threat intelligence feeds to stay informed about the latest threats and trends.
By staying informed about emerging cybersecurity threats, you can protect your startup’s digital assets and stay ahead of hackers. Remember, cybersecurity for startups is an ongoing process that requires regular monitoring and review to ensure the security of digital assets.
By incorporating the latest threat intelligence into your cybersecurity strategy, you can improve your incident response plan and respond more effectively to security breaches. Stay informed, stay ahead, and protect your startup’s digital future.