Reverse Image Search: A Powerful Tool for Finding Photo Origins
Reverse image search is a powerful tool for finding the origin of an image. This technique involves uploading an image to a search engine or using a dedicated reverse image search tool to find identical or similar images online. By using reverse image search, individuals can quickly identify the source of an image, track its usage, and verify its authenticity.
Several popular tools offer reverse image search capabilities, including Google Images, TinEye, and Bing Image Match. These tools use advanced algorithms to analyze the image and match it with similar images in their databases. By using these tools, individuals can find the origin of an image, identify potential copyright infringement, and verify the image’s authenticity.
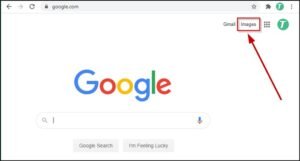
For example, Google Images allows users to upload an image or enter the image’s URL to search for similar images. TinEye, on the other hand, uses a proprietary algorithm to match images and provides a list of potential sources. Bing Image Match offers a similar service, allowing users to search for images using a variety of parameters, including image URL, file upload, or drag-and-drop.
By using reverse image search, individuals can take the first step in verifying the origin of an image. This technique is particularly useful for identifying images that have been manipulated or used without permission. By finding the original source of an image, individuals can ensure that they are using images responsibly and respecting the intellectual property rights of others.
Image Metadata: Uncovering Hidden Clues
Image metadata is a treasure trove of information that can help uncover the origin of an image. Metadata is “data that provides information about other data,” and in the case of images, it includes details such as the camera model, date and time of capture, location, and copyright information. By analyzing image metadata, individuals can gain valuable insights into the image’s history and authenticity.
There are several types of image metadata, including EXIF (Exchangeable Image File Format) data, IPTC (International Press Telecommunications Council) headers, and XMP (Extensible Metadata Platform) metadata. EXIF data is typically used by digital cameras to store information about the image, such as the camera model, aperture, and shutter speed. IPTC headers, on the other hand, are used to store information about the image’s content, such as the caption, keywords, and copyright information. XMP metadata is a more recent development that allows for the storage of additional metadata, such as the image’s author and creation date.
To access image metadata, individuals can use a variety of tools, including image editing software, online metadata viewers, and browser extensions. For example, Adobe Photoshop and Lightroom allow users to view and edit image metadata, while online tools like Jeffrey’s Exif Viewer and Metadata Viewer provide a quick and easy way to view metadata without downloading any software.
By analyzing image metadata, individuals can uncover hidden clues about the image’s origin. For example, EXIF data can reveal the camera model and serial number used to capture the image, while IPTC headers can provide information about the image’s content and copyright status. XMP metadata can also provide valuable insights into the image’s creation date and author.
Watermarks and Digital Signatures: Identifying Ownership
Watermarks and digital signatures are two techniques used to identify image ownership and verify authenticity. A watermark is a visible or invisible mark embedded in an image to identify the owner or creator, while a digital signature is a unique code that verifies the image’s authenticity and integrity.
Watermarks can be used to identify the owner of an image and prevent unauthorized use. There are two types of watermarks: visible and invisible. Visible watermarks are overlays that are placed on top of the image, while invisible watermarks are embedded in the image data and can only be detected using specialized software. Digital signatures, on the other hand, use encryption algorithms to create a unique code that verifies the image’s authenticity and integrity.
To detect and decode watermarks and digital signatures, individuals can use specialized software such as Adobe Photoshop or online tools like Watermark Detector or Digital Signature Verifier. These tools can help identify the owner of an image and verify its authenticity, making it easier to find the origin of an image.
For example, a photographer may use a watermark to identify their images and prevent unauthorized use. A digital signature can also be used to verify the authenticity of an image, ensuring that it has not been tampered with or altered in any way. By using watermarks and digital signatures, individuals can protect their intellectual property and ensure that their images are used responsibly.
In addition to watermarks and digital signatures, individuals can also use other techniques to identify image ownership, such as checking the image’s metadata or searching for similar images online. By combining these techniques, individuals can increase the chances of finding the origin of an image and verifying its authenticity.
Image Forensics: Analyzing Image Characteristics
Image forensics is a technique used to analyze image characteristics to determine the image’s origin. This involves examining the image’s compression artifacts, noise patterns, and color profiles to identify potential clues about the image’s history. By analyzing these characteristics, individuals can gain valuable insights into the image’s authenticity and potential manipulation.
Compression artifacts are a common characteristic of digital images. These artifacts can reveal information about the image’s compression history, including the type of compression algorithm used and the level of compression applied. Noise patterns, on the other hand, can provide clues about the image’s capture device and processing history. Color profiles can also be analyzed to determine the image’s color space and potential manipulation.
To analyze image characteristics, individuals can use specialized software such as Adobe Photoshop or online tools like Image Forensics Tool or FotoForensics. These tools can help identify potential clues about the image’s origin and authenticity, making it easier to find the origin of an image.
For example, a forensic analysis of an image may reveal that it has been compressed multiple times, indicating potential manipulation. Noise patterns may also reveal that the image was captured using a specific camera model or processed using a particular software. By analyzing these characteristics, individuals can increase the chances of finding the origin of an image and verifying its authenticity.
In addition to image forensics, individuals can also use other techniques to analyze image characteristics, such as checking the image’s metadata or searching for similar images online. By combining these techniques, individuals can gain a more comprehensive understanding of the image’s origin and authenticity.
Online Archives and Stock Photo Websites: A Treasure Trove of Image Origins
Online archives and stock photo websites are a valuable resource for finding image origins. These websites provide access to vast collections of images, often with detailed metadata and licensing information. By searching these websites, individuals can find the origin of an image and verify its authenticity.
Getty Images, Shutterstock, and Flickr are popular online archives and stock photo websites that offer a vast collection of images. These websites provide detailed metadata, including the image’s title, description, and licensing information. By searching these websites, individuals can find the origin of an image and verify its authenticity.
For example, Getty Images offers a vast collection of images, including historical and contemporary photographs. Shutterstock provides a vast collection of stock photos, illustrations, and vectors. Flickr offers a vast collection of user-generated images, often with detailed metadata and licensing information.
When searching online archives and stock photo websites, individuals can use various search techniques, including keyword searches, image searches, and advanced searches. By using these techniques, individuals can find the origin of an image and verify its authenticity.
In addition to online archives and stock photo websites, individuals can also use other resources to find image origins, such as social media and online communities. By combining these resources, individuals can increase the chances of finding the origin of an image and verifying its authenticity.
Social Media and Online Communities: Crowdsourcing Image Origin Detection
Social media and online communities can be a valuable resource for crowdsourcing image origin detection. By leveraging platforms like Reddit, Twitter, and Facebook, individuals can tap into a vast network of users who can help identify the origin of an image.
Reddit’s r/photography and r/imageidentification communities are popular platforms for crowdsourcing image origin detection. Users can post an image and ask for help identifying its origin, and the community can provide valuable insights and information. Twitter’s hashtag system can also be used to crowdsource image origin detection, with hashtags like #imageorigin and #photodetection.
Facebook groups like “Image Origin Detection” and “Photography Identification” can also be used to crowdsource image origin detection. These groups provide a platform for users to share images and ask for help identifying their origin.
When using social media and online communities for crowdsourcing image origin detection, it’s essential to provide as much information as possible about the image. This can include the image’s metadata, any visible watermarks or signatures, and any other relevant details. By providing this information, individuals can increase the chances of getting accurate and helpful responses from the community.
In addition to social media and online communities, individuals can also use other resources to find image origins, such as online archives and stock photo websites. By combining these resources, individuals can increase the chances of finding the origin of an image and verifying its authenticity.
Best Practices for Verifying Image Origins
Verifying image origins is a crucial step in maintaining the integrity of online content. To ensure the accuracy and authenticity of images, it’s essential to follow best practices for verifying image origins. In this section, we’ll summarize the key takeaways from our step-by-step guide and provide additional tips for verifying image origins.
Cross-validation is a critical step in verifying image origins. This involves verifying the image’s metadata, watermarks, and digital signatures to ensure consistency and accuracy. Critical thinking is also essential, as it allows individuals to analyze the image’s characteristics and identify potential red flags.
Transparency is also crucial when verifying image origins. This involves being open and honest about the image’s source and providing clear attribution. By following these best practices, individuals can ensure the accuracy and authenticity of images and maintain the integrity of online content.
In addition to these best practices, individuals can also use various tools and resources to verify image origins. These include online archives and stock photo websites, social media and online communities, and image forensics software. By combining these resources and following best practices, individuals can increase the chances of finding the origin of an image and verifying its authenticity.
By verifying image origins, individuals can ensure the accuracy and authenticity of online content. This is essential for maintaining credibility and trust in online communities. By following the steps outlined in this guide and incorporating best practices, individuals can take the first step towards verifying image origins and maintaining the integrity of online content.
Best Practices for Verifying Image Origins
Verifying image origins is a crucial step in maintaining the integrity of online content. To ensure the accuracy and authenticity of images, it’s essential to follow best practices for verifying image origins. By incorporating these practices into your workflow, you can increase the chances of finding the origin of an image and verifying its authenticity.
Cross-validation is a critical step in verifying image origins. This involves verifying the image’s metadata, watermarks, and digital signatures to ensure consistency and accuracy. Critical thinking is also essential, as it allows individuals to analyze the image’s characteristics and identify potential red flags.
Transparency is also crucial when verifying image origins. This involves being open and honest about the image’s source and providing clear attribution. By following these best practices, individuals can ensure the accuracy and authenticity of images and maintain the integrity of online content.
In addition to these best practices, individuals can also use various tools and resources to verify image origins. These include online archives and stock photo websites, social media and online communities, and image forensics software. By combining these resources and following best practices, individuals can increase the chances of finding the origin of an image and verifying its authenticity.
By following these best practices, individuals can ensure the accuracy and authenticity of images and maintain the integrity of online content. This is essential for maintaining credibility and trust in online communities. By incorporating these practices into your workflow, you can take the first step towards verifying image origins and maintaining the integrity of online content.